First Look at Brigade.sh: Simplify Event-Driven Workflows
Explore Brigade.sh, a powerful tool for automating and managing event-driven workflows in Kubernetes
Published on:
Aug 9, 2018Last updated on:
Dec 9, 2025What is Brigade?
Brigade, from Azure, is a Kubernetes native event-driven scripting tool where we can use JavaScript to script a structured container pipeline inside the cluster. It is well suited for CI and CD workloads such as automated testing, Github/GitLab hook integration, building and releasing artifacts. At the same time it is more flexible than traditional CI/CD tools, where we can write javascript functions that can be triggered by events and executed on the Kubernetes cluster as jobs or deployments.
Brigade’s major components
- Brigade controller is the central controller that controls Kubernetes Deployments. It listens for events starts workers to process them.
- Brigade Gateway is the default gateway that ships with Brigade, or we can write a custom gateway such as Gitlab Integration and deploy that on the cluster. Gateway receives triggers (such as webhook from Github/Gitlab) in to events.
- Brigade API is an API server used to access information about Brigade’s current and past workloads.
- Worker is responsible for executing the scripts as Kubernetes jobs that are created by the gateway.
- Job(s) are Kubernetes jobs which are launched by worker, they complete tasks that are written in javascript and provide the result back to worker.
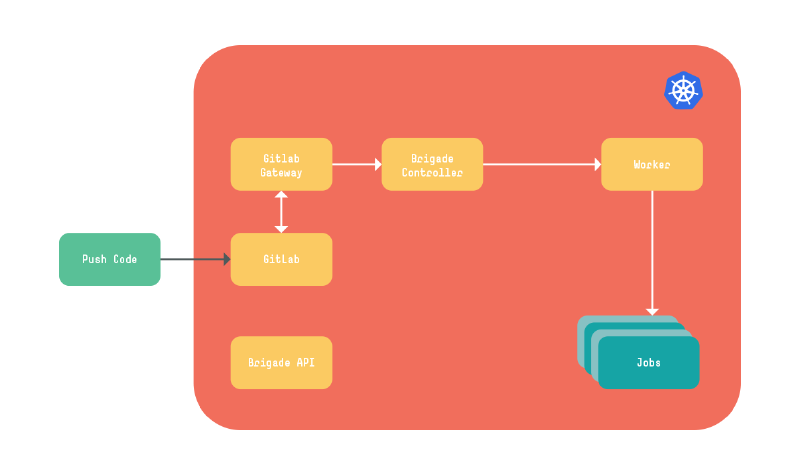
Figure - Brigade Diagram 1
Hands-on Brigade demo
This post will focus on Brigade integration with Gitlab, which uses a custom gateway.
Brigade can be easily installed with Helm on your Kubernetes cluster (or on your local “Docker for Windows/Mac”/ Minikube):
helm repo add brigade 'https://azure.github.io/brigade'
helm install -n brigade 'brigade/brigade'
Once Brigade is successfully installed on the cluster, you can create a Brigade project by using a command line client tool called brig (from Brigade version 0.16 version) or a Helm chart. The newly created project will be deployed as a Kubernetes Secret. Brigade projects provide the necessary context for executing Brigade scripts. They provide permission to run scripts, authentication for some operations, configuration for VCS, and secret management for Brigade scripts.
How do I create a new Brigade project?
Create a new Brigade project using the following values.yaml:
project: "brigade-project-name"
repository: "git lab repo url"
cloneURL: "git lab repo url to clone the project"
sharedSecret: "MySharedSecret"
vcsSidecar: "Azure/git-sidecar:latest"
sshKey: |-
-----BEGIN RSA PRIVATE KEY-----
YOUR SSH PRIVATE KEY
-----END RSA PRIVATE KEY-----
And install the project again using helm:
helm install --name brigade-project-name -f values.yaml
Next, Create your project (source code) in your local git repo along with the brigade.js file in the root directory. brigade.js is the standard name for a JavaScript file that contains one or more Brigade event handlers. The following brigade.js file contains a simple event that will be executing go test in your pipeline.
brigade.js :
const { events, Job , Group} = require("brigadier");
const dest = "$GOPATH/src/awesome.git.repo/you/temp/brigade-demo";
events.on("push", (e, p) => {
console.log(e.payload)
var test = new Job("test", "golang:1.9")
test.tasks = [
"mkdir -p " + dest,
"cp -a /src/* " + dest,
"cd " + dest,
"go get -u github.com/golang/dep/cmd/dep",
"dep ensure",
"make test"
];
// Run tests.
test.run();
});
events.on("error", (e, p) =>{
console.log(e)
})
Brigade Gitlab integration
Next, install the Brigade Gitlab Gateway`:
git clone 'https://github.com/lukepatrick/brigade-gitlab-gateway'
cd brigade-gitlab-gateway
helm install --name gl-gw './charts/brigade-gitlab-gateway'
As soon as the Brigade Gitlab Gateway is installed, create a new GitLab project to configure webhook. In your GitLab project, go to:
Settings -> Integrations
Depending on your set up, Kubernetes and the GitLab Gateway will determine your externally accessible host/IP/Port. Out of the box the gateway sets up as LoadBalancer, or you can update the helm chart to set the service type as ClusterIP and the Gitlab webhook integration URL can be configured as a local service dns record:
http:/<brigade-gitlab-gateway-service-name>.<namespace>.svc:7746/events/gitlab
The Secret Token will be the same string used in the Brigade Project values.yaml sharedSecret property.
Check the boxes for the Trigger events to publish from the GitLab instance. SSL is optional.
Once webhook is configured push your code. A push event will be triggered and a Brigade Job will be started by a worker, and is executed as a pod. You can view the pipeline process in a dashboard called kashti which comes with the Brigade bundle:
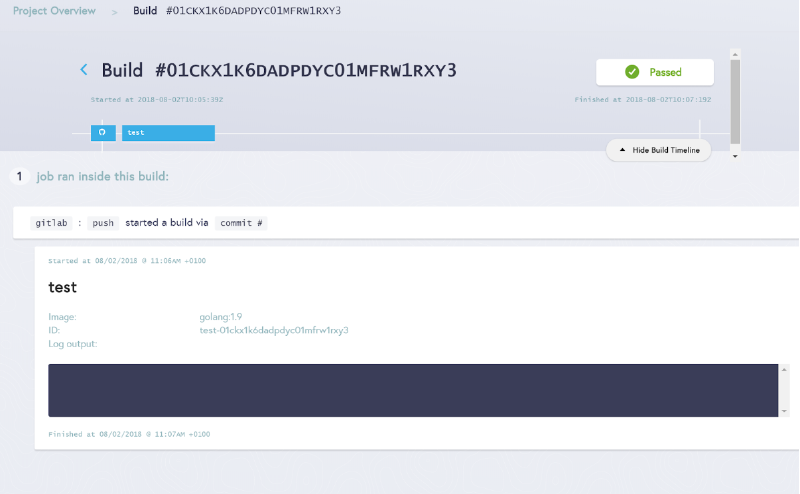
Figure - Kahsti
A DevOps Engineer’s final thoughts on Brigade
As we all know, Kubernetes is awesome, but Brigade brings new dimensions to Kubernetes and leverages the platform to build a CI/CD solution, serverless/Function as a Service (FaaS) platform without hassle.