A Junior Developer's favourite takeaways from KubeCon India 2025
Kubernetes security and policy automation benefits for Platform Engineering teams
Published on:
Sep 26, 2025Last updated on:
Feb 17, 2026This blog is part of our KubeCon India series, we recommend reading the rest of the posts in the series:
- KubeCon + CloudNativeCon India 2025: Technical Insights from Hyderabad
- KubeCon + CloudNativeCon India 2025: Four standout Cloud-Native technologies
- A Junior Developer's favourite takeaways from KubeCon India 2025
Introduction
KubeCon India 2025 showcased the rapid evolution of Cloud-Native security and governance practices for Platform Engineers. Two sessions particularly stood out for their practical approach to embedding security controls directly into Kubernetes platforms, demonstrating how policy automation can enhance rather than hinder development velocity.
Security that works behind the scenes
Guard your network with Kyverno and Envoy | Sanskar Gurdasani (AccuKnox) & Swastik Gour (InfraCloud Technologies)
How policy and proxy can work together to keep Kubernetes clusters secure by default.
“Guard your Network with Kyverno and Envoy” delivered by Sanskar and Swastik demonstrated how Kyverno, a policy engine for Kubernetes, can be combined with Envoy, a powerful service proxy, to strengthen network security. The talk demonstrated how policies can be used for both configuration checks and for securing workloads at runtime.

The approach demonstrated required zero application code changes allowing developers to deploy services normally, while network security policies are enforced automatically through the service mesh. Kyverno handles policy definition and validation, while Envoy manages traffic control and security enforcement at runtime. This addresses a common challenge in platform engineering. Implementing security controls consistently across multiple development teams proves difficult when enforcement relies on manual processes or developer training. When security becomes a platform feature rather than a development responsibility, you eliminate inconsistency and reduce the cognitive load on application teams.
The demonstration showed how Common Expression Language (CEL) policies can be embedded into service mesh configurations, creating dynamic security controls that adapt to workload requirements without manual intervention.
For readers who want further technical details:
- The demo used Envoy’s External Authorization filter to call a stand alone Kyverno gRPC service on port
9081(no admission controller required for this path). - Policies written in YAML with CEL expressions extracted the
Authorizationheader, decoded the JWT, and applied deny / allow logic returning 401 (no header), 403 (JWT role = guest) or 200 (JWT role = admin). - A
failurePolicy: Failpattern ensured unknown or evaluation error cases defaulted to deny, and the gRPC endpoint was secured with certificates issued by cert-manager.
The key takeaway was the importance of treating security as a design principle rather than an afterthought. Kyverno’s ability to enforce declarative rules, paired with Envoy’s control over live traffic, provides consistency and predictability at the network layer. Together, they offer a model where automated guardrails reduce operational risk while enabling teams to focus on delivering applications.
Policy as Code for Platform governance
Kubernetes Policy as Code for Platform Engineers | Sonali Srivastava (InfraCloud Technologies), Mohd Kamaal & Kushal Agrawal (Independent)
Turning governance into code to make Kubernetes platforms safer and easier to run.
“Kubernetes Policy as Code for Platform Engineers” by Sonali, Mohd and Kushal broke down the philosophy of “Policy as Code” in Kubernetes, showing how teams can manage security and compliance best practices through version controlled policies.

It was insightful how Policy as Code can transform governance from a manual oversight function into an automated platform capability. When done correctly, policies are written in YAML, stored in Git repositories, reviewed through pull requests, and deployed via CI/CD pipelines. This approach will eliminate any configuration drift between environments and ensures consistent rule application across clusters.
The practical examples from the talk included policies that automatically add security labels, prevent privileged containers, enforce resource limits, and generate supporting resources like NetworkPolicies. These policies execute at deployment time, and provide immediate feedback to developers when workloads don’t comply with their organisational standards.
The speakers also shared a few practical tips:
- Teams can use kyverno-cli to simulate policy behaviour locally or in CI pipelines, and Chainsaw, a YAML driven end to end test runner to verify rules before rollout.
- They highlighted Kyverno 1.15 features such as new CEL based policy types with helpers like resource.get/list, http.get/post and SubjectAccessReview, which reduce boilerplate context blocks and align with upstream Kubernetes.
- Migration guidance focused on moving existing policies to CEL expressions and proving parity with Chainsaw tests before switching.
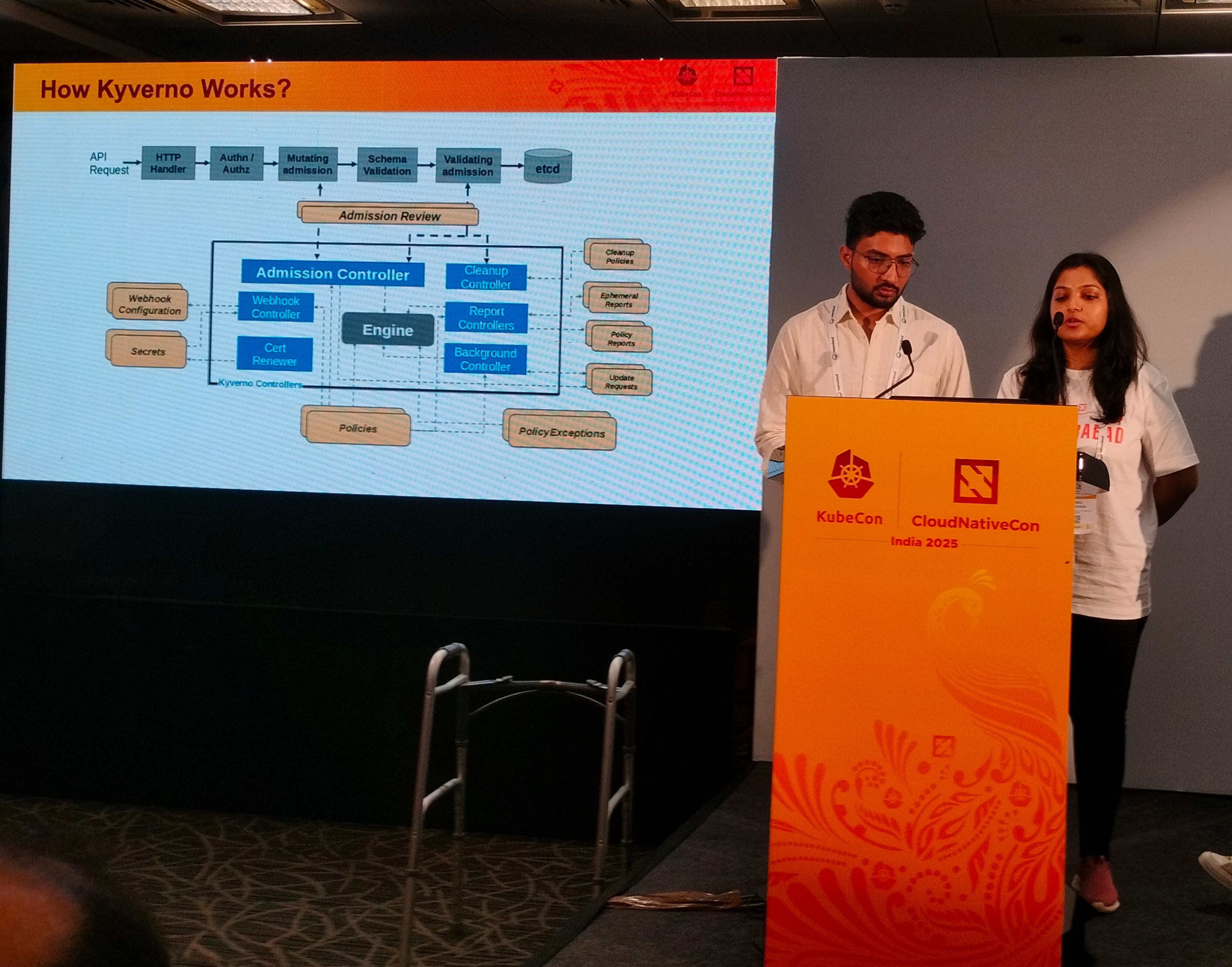
My key takeaway was that by adopting this policy as code you can transform governance from an overhead that is imposed on development teams into something that adds benefit to their day to day role. It’s great to see that policies can be versioned, tested, and deployed like code, and that they can be improved iteratively and adapted to any changing requirements.
My closing thoughts
The Platform Engineering shift
From both sessions, and throughout other KubeCon conversations, it was apparent there seems to be a fundamental shift in Kubernetes operations and how security is included rather than an add-on. Modern platforms are now embedding good practices into the infrastructure creating systems where adopting best practices becomes easy. Previously, we have seen how manual security reviews and configuration checklists don’t scale with team and platform growth, but now we have Platform-level enforcement through tools like Kyverno allowing security to become more sustainable, aligning it with the existing development workflows.
Why this matters for Platform teams
The Cloud-Native ecosystem continues to evolve rapidly. We are now seeing much more focus on technical innovations that solve human and operations problems alongside alongside pure technical challenges. Both Kyverno and Envoy succeed because they reduce operational burden while improving security posture. This allows Developers to gain confidence to ship features quickly, as the security controls work automatically. The result is faster delivery cycles with better security outcomes. These approaches are particularly valuable in multi-team environments where consistency becomes challenging to maintain through manual processes. We now have the ability to catch policy violations early in CI/CD pipelines which creates shorter feedback loops and fewer production issues.
If you want to dive deeper into the technologies discussed in this blog, check out:
This blog is part of our KubeCon India series, we recommend reading the rest of the posts in the series:
- KubeCon + CloudNativeCon India 2025: Technical Insights from Hyderabad
- KubeCon + CloudNativeCon India 2025: Four standout Cloud-Native technologies
- A Junior Developer's favourite takeaways from KubeCon India 2025
